Mcard Vulnerability
Wednesday, April 6, 2005
After investigating the security of the Mcard magnetic card system at the University of Michigan, which is used for student and faculty identification cards, I discovered that it is trivial to forge anyone's Mcard given only their UMID/uniqname.
Introduction
The University of Michigan's student/faculty identication cards, Mcards, are used for a variety of uses such as photo ID, meal plans, Entree Plus, TCF debit card, and access to dorms, computer labs, and other University buildings. Mcards are issued to incoming students and new faculty and staff when they join the University. They possess a magnetic strip on the back that is used by readers across the campus to authenticate the identity of the cardholder.

Mcard Contents
Mcards are standard 3-track LoCo ISO 7811-2 PVC magnetic cards. The magnetic reader/writer used for experimentation is MAKStripe's R2TAO. The following is the data contained on the magnetic tracks of my personal Mcard:
Track 1: %B6008476891430812^OBERHEIDE/J^0707120?V
Track 2: ;6008476891430812=07071200000000000?=
Below is the important information to extract from the card:
Name: OBERHEIDE/J
Account Number: 6008476891430812
Expiration Date: 07/07
The account number itself is made up of several components:
600847 68914308 1 2
|____| |______| | |
| | | |
A B C D
- Part A: identical prefix for all Mcards
- Part B: UMID of the cardholder
- Part C: revision of the card, starting at 1, incrementing each time it is replaced
- Part D: Luhn checksum of the account number
Mcard Forgery
After thorough experimentation, I was able to determine that the card readers used by the University only read a subset of the data contained on the card, namely the account number on track 2 of the card. This simple number is all that is necessary to authenticate a cardholder's identity.
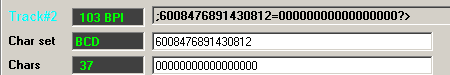
Obtaining a victim's UMID is a trivial task, as UMIDs are not meant to be secret numbers. A web query interface is even available that translates uniqnames to their corresponding UMID. As most victims will still have the first revision of their card, it is relatively safe to assume that value of Part C is 1. Even if the victim has previously lost their card and has gotten a replacement, it is trivial to re-encode the account number with a 2 if the first attack does not succeed. Finally, the last number can be calculated by using the Luhn algorithm.
Given these circumstances, it is trivial to construct the account number of an arbitrary victim and impersonate the magnetic Mcard identity of that victim. Potential attacks include depleting the victim's Entree Plus balance, entering University buildings under the victim's identity, and stealing money from a linked TCF bank account.
Given the ease of executing such an attack, the financial and legal implications of this flaw are very severe. The University has been made aware of this vulnerability and will be rolling out a campus-wide solution in the near future.