xkcd Malware Visualization
Friday, November 30, 2007
A recent xkcd comic related to malware visualization is eerily similar to a system we're currently running at the University of Michigan.
The xkcd Comic
Our System
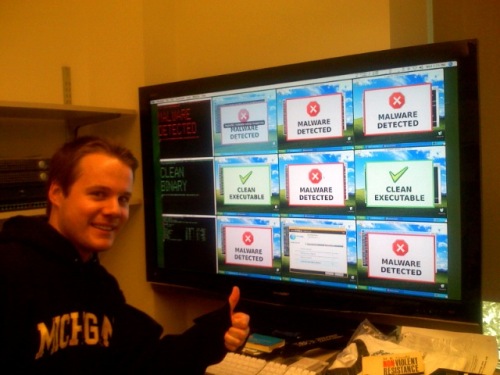
The system pictured is a production version of an architecture we proposed last year at HotSec '07 (paper, presentation), essentially a network-based AV service. The backend analysis system consists of Xen-based virtualized containers which host various detection engines. Candidate executables/files are acquired by a lightweight host-agent (hooking CreateProcess on Win32, Dazuko on Linux/BSD, etc) and transmitted to the backend for analysis by a bajillion (ok, maybe only 12) antivirus and behavioral engines. We currently employ antivirus engines from Avast, AVG, BitDefender, ClamAV, F-Prot, F-Secure, Kaspersky, McAfee, Symantec and Trend Micro. We also have two behavior engines, Norman Sandbox Analyzer and CWSandbox, to provide runtime behavioral profiles for candidate executions. This model has numerous advantages including significantly increased detection coverage, centralized management, and post-infection forensics. The photo shows our beautiful 52" LCD screen displaying the output of the various Xen VMs hosting the detection engines and the real-time detection results of the analysis of a malware sample.