Dam Burst

Description
Dam Burst is a simple utility that allows an unprivileged user to disable the censorship functionality of the Green Dam Youth Escort software. Dam Burst operates by injecting code into a running application and removing the Green Dam hooks that enable it to monitor and block user activity, effectively restoring the running application to its original uncensored state.
Unlike other tools that disable or uninstall the Green Dam software, Dam Burst does not require administrative privileges. Since Dam Burst can be run as an unprivileged user to disable the Green Dam censorware in currently running applications, it is very effective in situations where the user is restricted from obtaining administrator privileges and may wish to avoid censorship (eg. public/internet cafe computers that the user may not own).
As a pleasant side effect, disabling the Green Dam components within a running process actually increases the security of the end host as the vulnerable code paths within the Green Dam software are no longer exploitable by an attacker.
Download
Downloads have been archived.
Technical Details
At its core, Green Dam employs userspace API hooking to interpose on user activity and enforce its censorship functionality. When a new program is started, Green Dam will inject several DLLs into the address space of the new process and execute its hooking routines via CreateRemoteThread(). Green Dam also uses SetWindowsHookEx() to monitor keyboard (WH_KEYBOARD), mouse (WH_MOUSE), and messaging activity (WH_MSGFILTER), and Winsock Layered Service Providers (LSPs) to interpose on common network/socket operations.
Since Green Dam uses userspace hooking within the address space of a user-owned process, we can inject our own code into a running process as an unprivileged user, remove Green Dam’s hooks, and restore the process to its original non-censored state. To “burst” a process, we inject our Dam Burst DLL into the target process and execute our unhooking routines. Our routines invoke Green Dam’s publicly exported API (InjectLibrary() in InjLib32.dll) to reverse the API hooking, use UnhookWindowsHookEx() to remove the Windows keyboard/mouse/message hooks, and patch the in-memory image of the Winsock LSP hooks (DBFP_* in SurfGd.dll) to semantic NOPs to disable Green Dam’s networking eavesdropping.
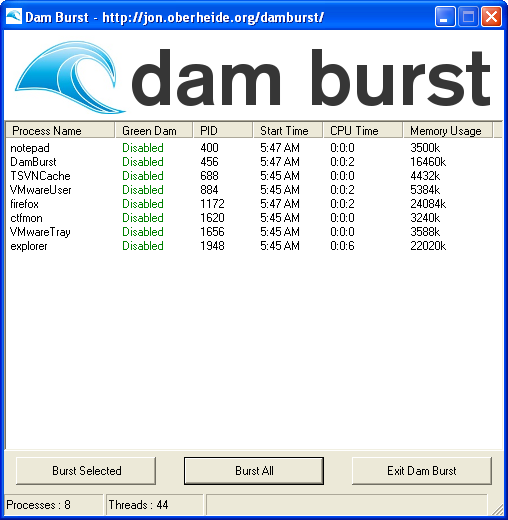
Screenshots
Before bursting:
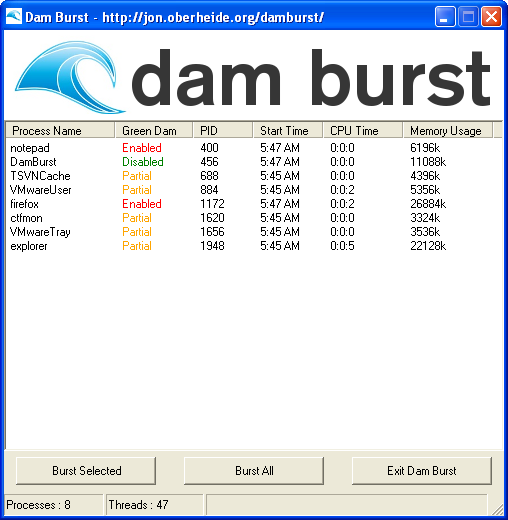
After bursting: